While job offer scams are common and most people know how to spot them, there are always a few that may slip through the cracks. In this quick write up I am going to give an example of said job offer that I received on linkedin, last week.
There were some unique traits about this particular job scam that caught my attention and sparked my curiosity. First I got an InMail from a recruiter (Linkedin’s Premium Feature to contact non-contacts) stating that they’re from “Mitsumi Electric Co. Ltd” a Legit Japanese company and it’s listed on the user’s profile.

Like most people, I googled the company and the person I was supposed to contact – everything looks legit! Mr. Adachi is listed as an executive director – seems legit.
Before I got firing off emails I check the domain “mitsumi-jp.com” where the email is supposed to go. Most users won’t notice, but once you visit the site listed above it redirects to the official Mitsumi website which is actually “mitsumi.co.jp”. A website redirection is exactly what it sounds like- it’s when you go to one web address and it forwards you to another web address usually without warning.

The Email
This is the email I received below, as you can see, it sounds too good to be true, however for a vulnerable person out of work – this scam might work! (Nigerian Scammers are still a thing!)

From the highlights above you notice the perpetrator(s) are using the correct company site in the email to further convince an unsuspecting job seeker. I won’t go into details about the actual email (grammar mistakes aside), however I would dive a bit deeper Into the URL redirections, Domain Name System (DNS) and WHOIS information to further point out why this is a scam and how you too scan use these steps in the future.
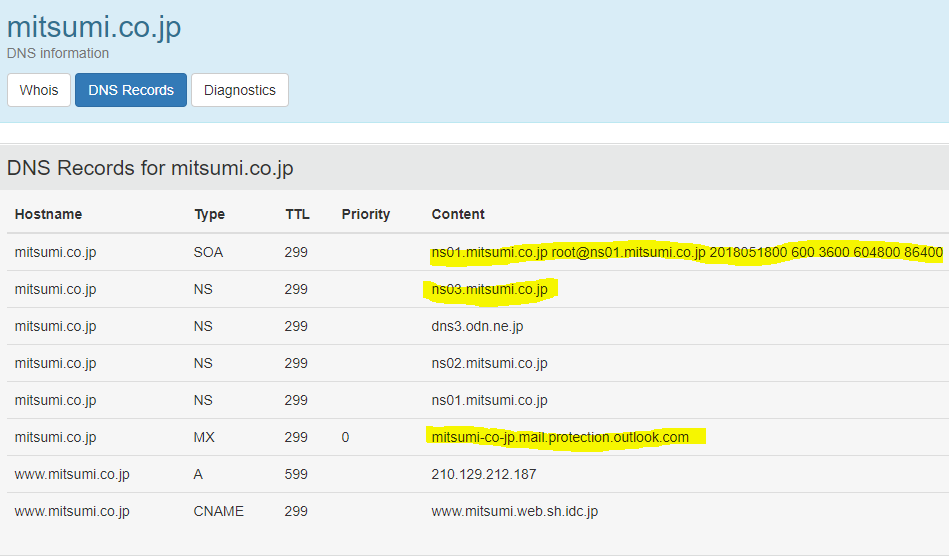
First I checked the DNS records and registration data for the official site using a free whois service.

This is the data that should be returned for any big company, the organization details properly listed and not blocked or registered by proxy. Another good indication is the Name Servers (Line 4) after the “ns01.” it is followed by the original domain name (web url), this means that Mitsumi host their own DNS servers (good sign). Another good sign was that the registration date is listed as “1996/07/04”, which is good because this information cannot be falsified.
Now on to the fake “mitsumi-jp.com”.

Right away there’s red flags here.
- Name of registering organization is protected.
- The Domain was recently registered “2019-1-24”
- The name servers are hosted by a third party, in this case “ClouDNS“.

Extras….
This is the email header which should give us more red flags… Zoho.com is a third party email hosting service – while a legitimate company it has a tendency to be abused. Also I would point out below the official Mitsumi has their own mail server, in the DNS records it’s listed as an MX record ( mitsumi.co.jp MX 2990 mitsumi-co-jp.mail.protection.outlook.com ).

Real Mail Server
If you have made it this far, thanks for reading and don’t hesitate to use to the contact form for questions or feedback. Stay woke and vigilant out there in the Wild Wild Web!
Cheers,
Sean

So What are your findings ? What do you think these guys are up to ?
Hi George, with nature of the job description this scam seems more aligned with check fraud where the perpetrators send you a check and you are to send a percentage of it to them. Once this is done the check bounces and you’re on the hook from your bank.
I got a similar offer this week on LinkedIn from an executive at Nippon Corporation. Thing is, their website careers section has the same blurb and seems legit, right?
http://www.nipponcorporation.jp/careers.html
Here is another one, looks like this is becoming a recent trend. Beware….
http://www.adachi-kk.co.jp/en/
Got one from http://www.adachi-kk.co.jp/en/ as well.
Thank you for all of your information and work. I jus received the same type of email. Folks its a scam. If it sound too good to be true its probably is not.
see: https://www.consumeraffairs.com/news/scam-alert-the-company-is-real-but-the-job-offer-is-fake-022015.html
The Chairman of Adachi sent me a really nice Memorandum of understanding!
Currently being contacted by them as well, even sent a check. Supposedly they want me to accept payments for them withhold%7 and they’ll pay me$5k a month, everything I can find is legit.
Hello Tyrone, I have received the same offer and was looking for this thread . What has been your experience . Was it a scam ?
I have learn some excellent stuff here. Definitely value bookmarking for
revisiting. I surprise how a lot attempt you puut to create
thhe sort oof wonderful informative website.